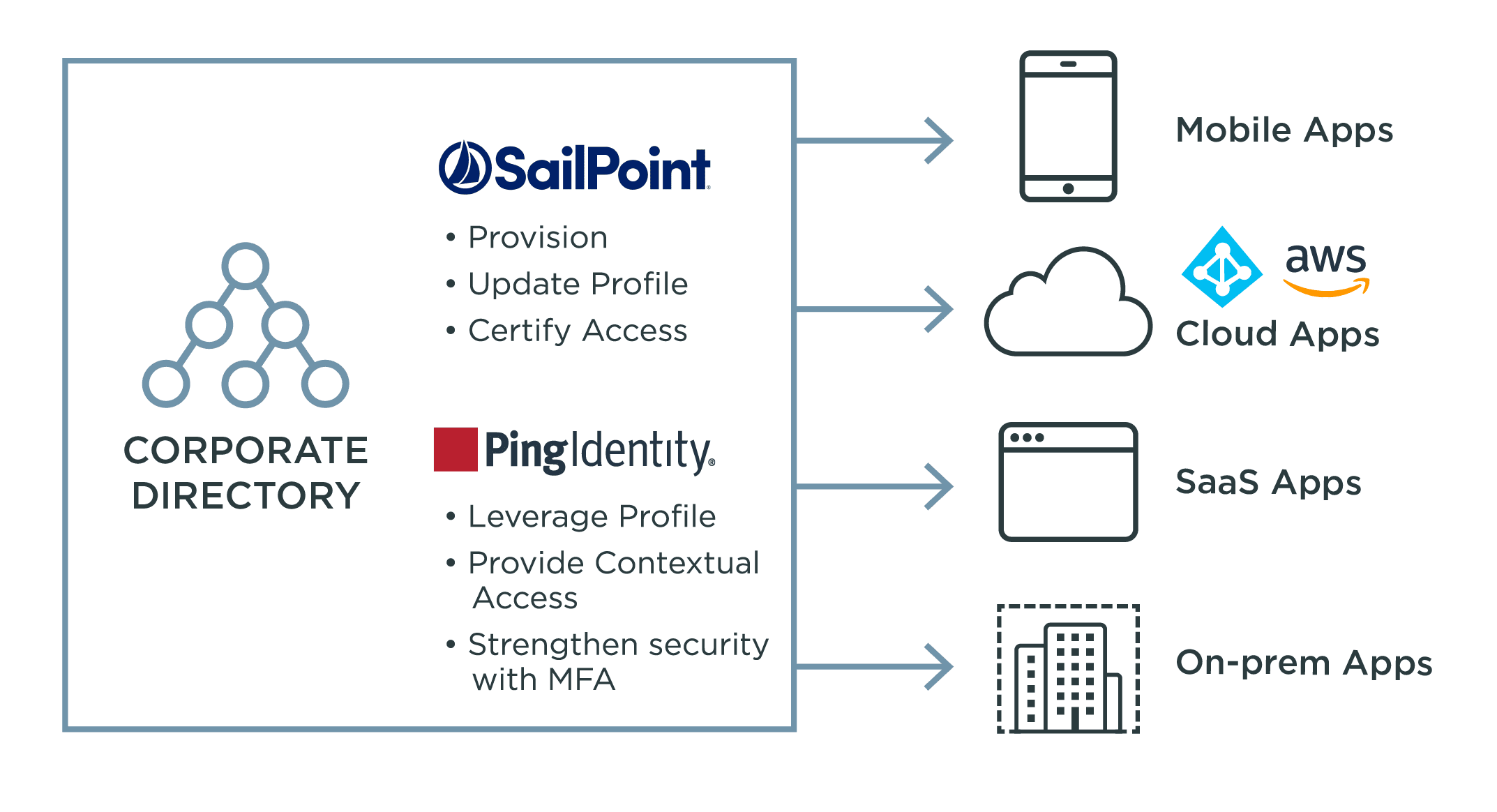
Introduction
Identity and access management (IAM) and identity governance and administration (IGA) work hand-in-hand to control access to resources, prevent data breaches, and comply with regulations. IGA isn't something offered by Ping, but we work with partners that provide this crucial solution. Read on to learn more about IGA, its importance in any security strategy, and how IGA and IAM work together.