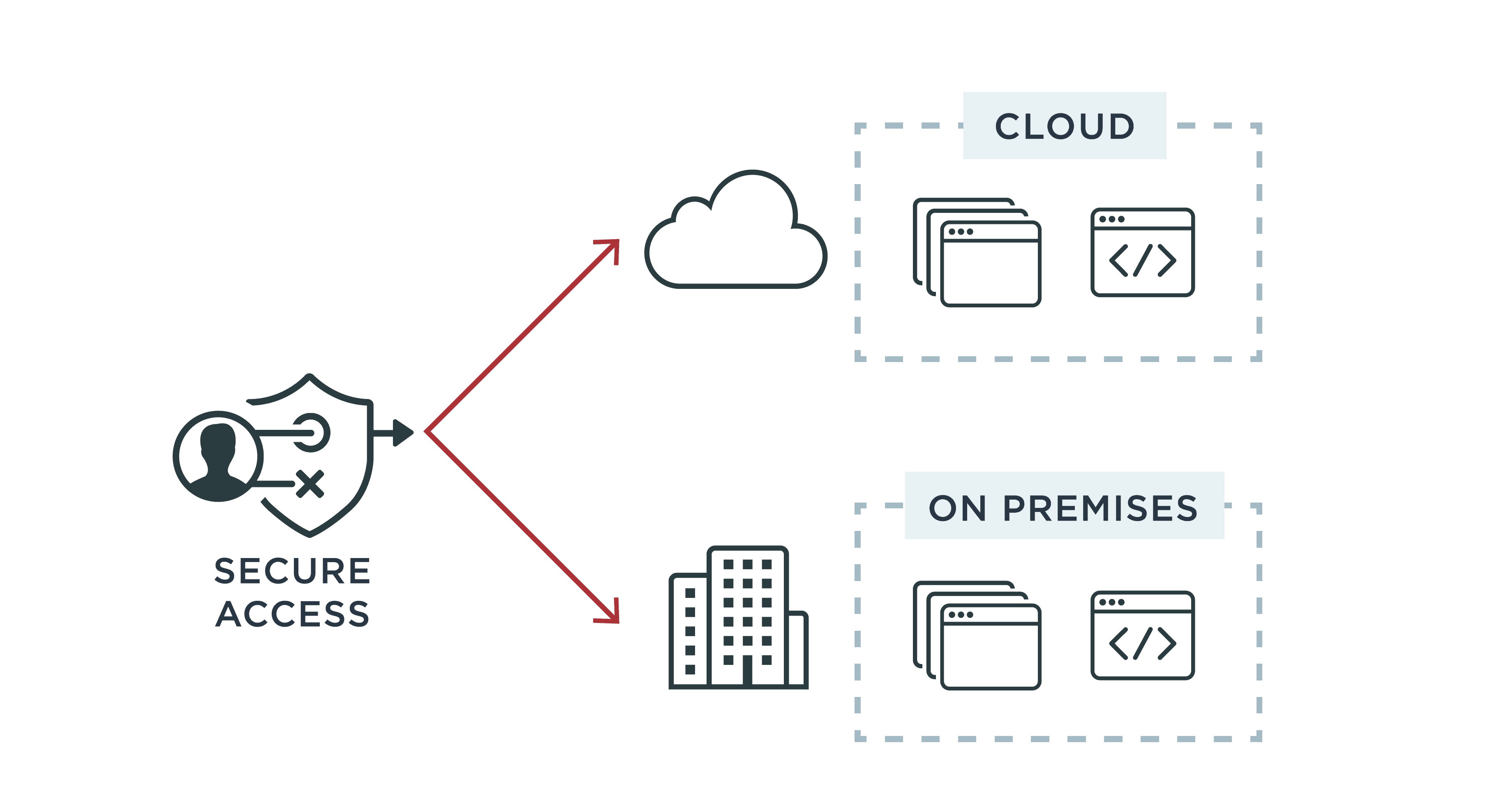
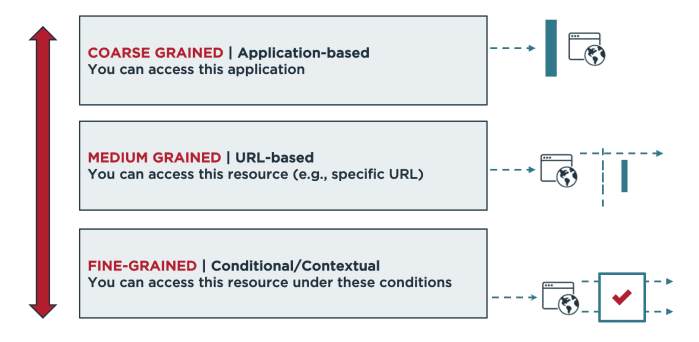
Controlling access to data and networks is a high priority for any organization. Enterprises use access control, also known as authorization, to grant access to resources using predetermined or customized permissions based on the user's role, identity attributes or risk factors.
Protecting access to customer data is also critical, and it's driven by three main factors: data privacy regulations, enterprise security needs and customer experience expectations. Ensuring a good customer experience as well as security and regulatory compliance can be difficult given the number of apps and APIs involved, along with the number of people and processes required to make necessary changes and updates.
Let's look at two access control options:
- Role-based access control (RBAC) enables access to resources or information based on user roles. These roles might be defined by job titles, departments, locations and/or specific duties and responsibilities.
- Attribute-based access control (ABAC) is a more flexible approach to authorization decisions, using additional information (attributes) to inform policy decisions. Moving beyond roles allows the use of granular attributes, including contextual attributes, in order to authorize an individual's access.
Read on to learn more about RBAC and ABAC, including differences, pros and cons.